
It's 3 AM, and Rachel, a Supply Chain Security Lead at a Fortune 500 company, gets an alert: "Unusual update pattern detected in vendor software." Her heart skips a beat. This is exactly how the SolarWinds attack started. But this time, thanks to their new security measures, they caught it early.
Rachel’s company transformed its approach from hope-for-the-best to a robust AI-powered defense system.
Here are some supply chain security statistics that will make start sweating in your bed at 2:00 in the morning:
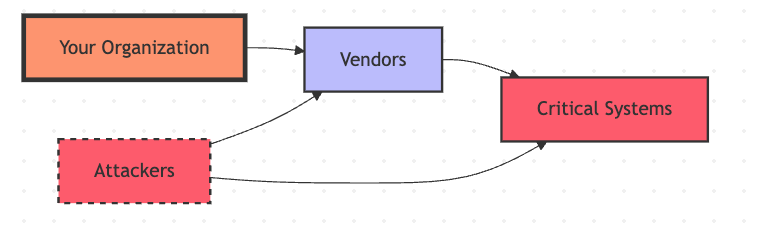
Think of your organization as the king, vendors as your pieces, and attackers as those trying to checkmate you. Every move matters.
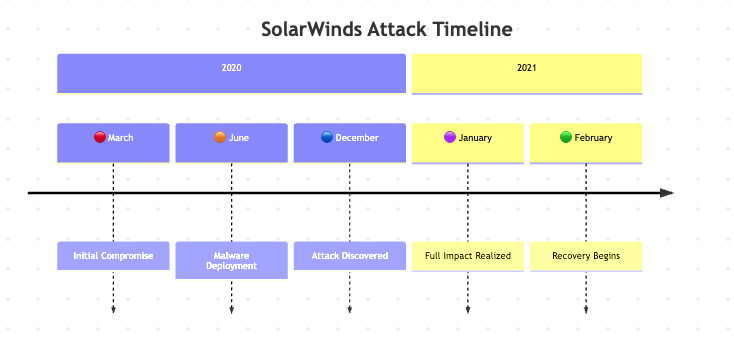
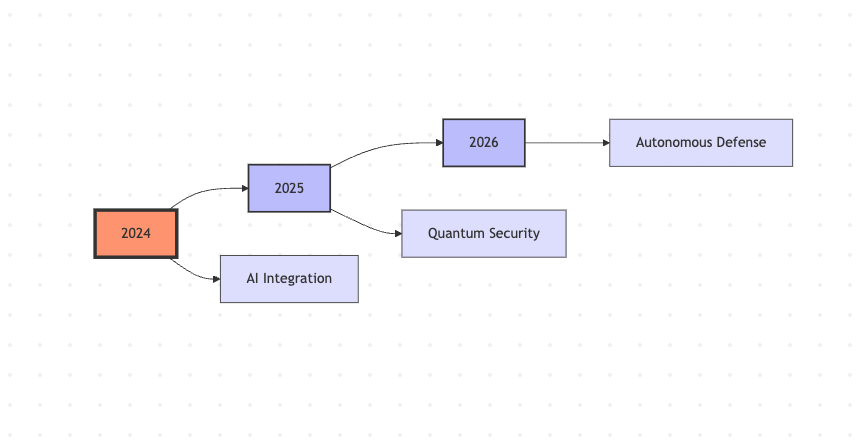
Timeline:
These aren’t isolated incidents. The last few years have seen a dramatic rise in targeted attacks on software supply chains.
Explore the Top 10 Major Software Supply Chain Attacks to see how attackers exploited real-world vulnerabilities across industries.
Impact:
At we45, we specialize in helping organizations build secure and resilient system from software supply chains to cloud-native deployments. Learn more about our enterprise security services.
Want to go beyond theory? Learn to break and secure software supply chains in real-world scenarios with hands-on labs and guided training on AppSecEngineerIn the world of cybersecurity, your supply chain is only as strong as its weakest link. And trust me, there's always a link that thinks it's stronger than it actually is!
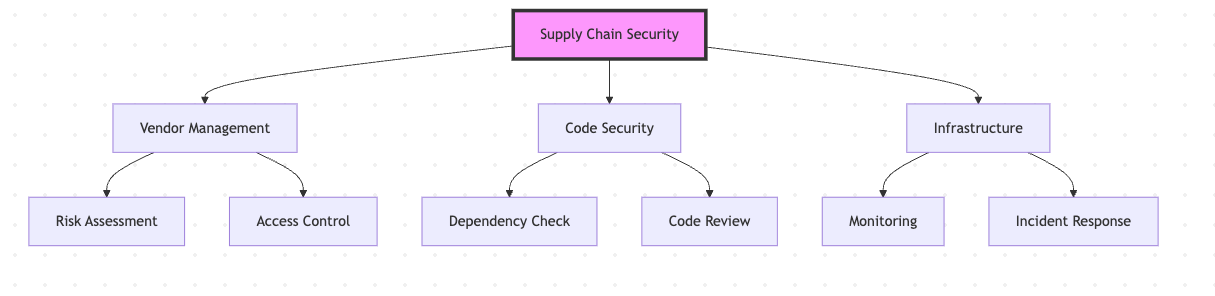
Supply chain security is a critical component of modern organizational security.
Remember: The best time to start securing your supply chain was yesterday. The second-best time is now. With the right tools, training, and mindset, you can build a resilient supply chain that protects your organization's assets and maintains customer trust.
With we45’s expert-led supply chain security services, you can get hand-on guidance on making sure that your organization is not going to be the next headline.
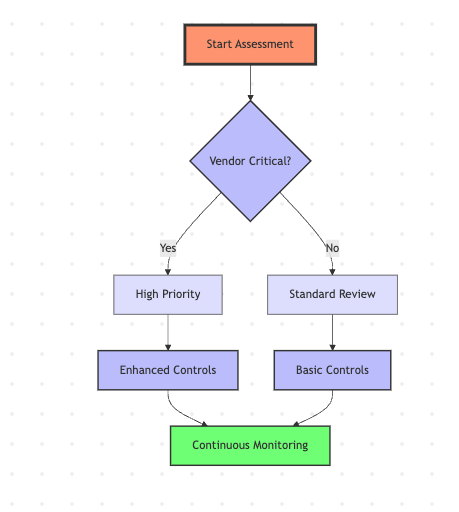
Begin with a thorough assessment: Inventory all vendors and dependencies, Evaluate critical systems, Assess current security measures, Identify gaps and priorities, Develop an implementation plan
It's not a trade-off! Modern DevSecOps practices show that security can accelerate development by: Catching issues early Automating security checks, Reducing technical debt Streamlining compliance
A comprehensive approach includes: Dependency scanners, Vendor risk assessment tools, CI/CD security tools, Monitoring solutions Incident response platforms
FinTech companies face unique challenges: Stricter regulatory requirements, Higher customer data sensitivity, Real-time transaction security, Complex vendor ecosystems
Healthcare supply chain security focuses on: Patient data protection, Medical device security Regulatory compliance (HIPAA), Vendor access management
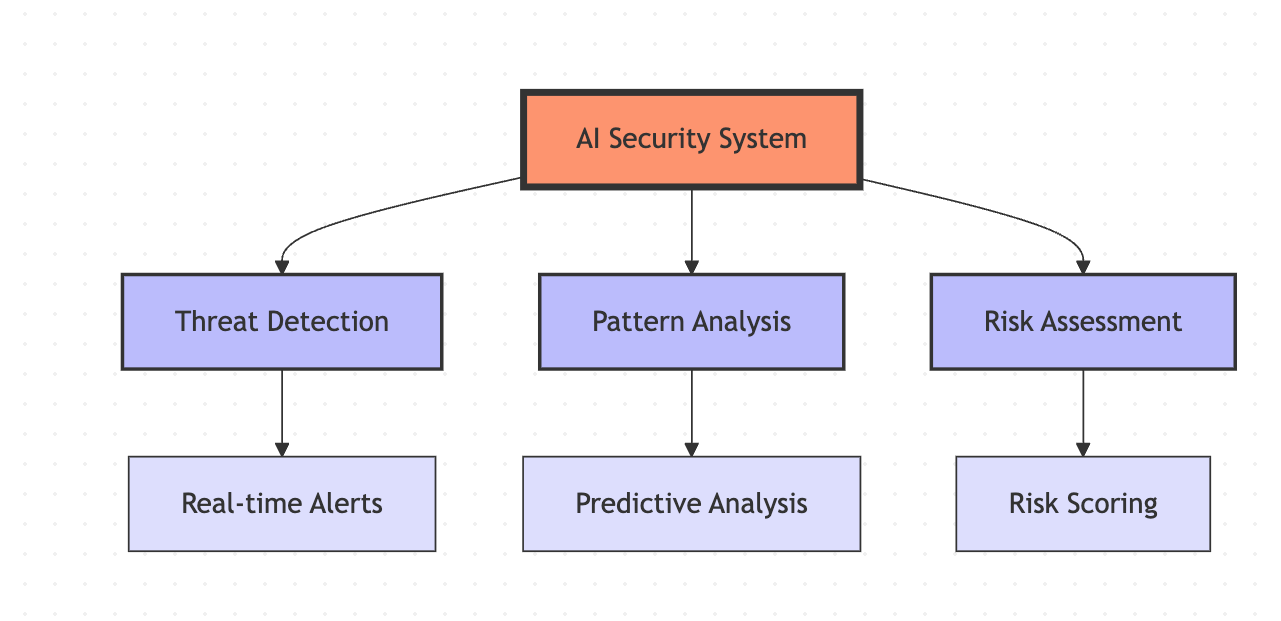
AI is revolutionizing supply chain security through: Predictive threat detection, Automated risk assessment, Real-time monitoring Intelligent response systems
Keep an eye on: AI-powered attacks, Quantum computing threats, IoT device vulnerabilities, Cloud service compromises
Use a collaborative approach: Clear communication, Shared security goals, Mutual benefit demonstration, Gradual implementation
Automation is crucial for: Continuous monitoring, Vulnerability scanning, Incident response, Compliance verification
Costs vary based on: Organization size, Current security posture, Industry requirements, Implementation scope