
The open-source software ecosystem, a cornerstone of modern development, faced a series of coordinated and highly sophisticated supply chain attacks in September 2025. Rather than targeting a single company or product, the attackers struck at the heart of the JavaScript ecosystem, using social engineering and novel malware to compromise the infrastructure of trust that developers and organizations depend on.
The campaign began with phishing attacks that hijacked maintainer accounts for major npm packages like debug and chalk, which are downloaded billions of times each week. Attackers injected malicious payloads that acted as crypto-stealers, before escalating to a more dangerous threat: the self-propagating Shai-Hulud worm. This worm spread autonomously to over 200 packages, even reaching projects managed by prominent organizations such as CrowdStrike, introducing an alarming new capability in software supply chain attacks.
Although the attackers netted only a few hundred dollars in stolen cryptocurrency, the true cost was far greater. Organizations were forced into emergency audits, rapid credential rotations, and other costly disruptions, revealing how one breach can ripple into a systemic crisis. The attacks suggested that financial gain may not have been the primary goal; instead, they appeared designed to test the scalability of new attack methods and study defensive responses, posing fundamental questions about the resilience of the open-source model itself.
The entry point for this far-reaching supply chain compromise was a classic, yet highly effective, social engineering campaign. The attackers meticulously crafted a phishing scheme that exploited human trust and a false sense of urgency, proving once again that the human factor remains the weakest link in the software supply chain.
The attack started with a convincing phishing campaign that impersonated official npm support. To make their messages look legitimate, the attackers registered a fake domain (npmjs.help), and used it to send emails warning developers about urgent two-factor authentication (2FA) updates. By exploiting developer fatigue and time pressure, the attackers tricked recipients into handing over their credentials.
One npm maintainer, Josh Junon, admitted he fell for the scam while checking messages on his phone, unintentionally giving attackers full access to his account and publishing rights. This incident shows how even experienced developers can be deceived by well-crafted social engineering. It also highlights a larger weakness: the open-source ecosystem often relies on just a handful of unpaid maintainers, meaning the security of thousands of projects can hinge on the vigilance of individuals who may lack resources or support.
The compromise of a single maintainer account was all that was needed to unleash a cascading attack across the ecosystem. With control over accounts like that of the well-known developer qix and Josh Junon, the attackers gained publishing rights to a portfolio of highly popular packages that are foundational to countless projects. This included libraries such as debug, chalk, and supports-color, which collectively see billions of weekly downloads. By poisoning these packages at the source, the malicious code was automatically distributed downstream to every developer and automated build process that installed or updated them, demonstrating how a single point of failure can have a disproportionately large impact.
The speed of the attack's progression and the community's swift response highlight the urgency of modern supply chain threats.
Table 1: Key Timeline of Events
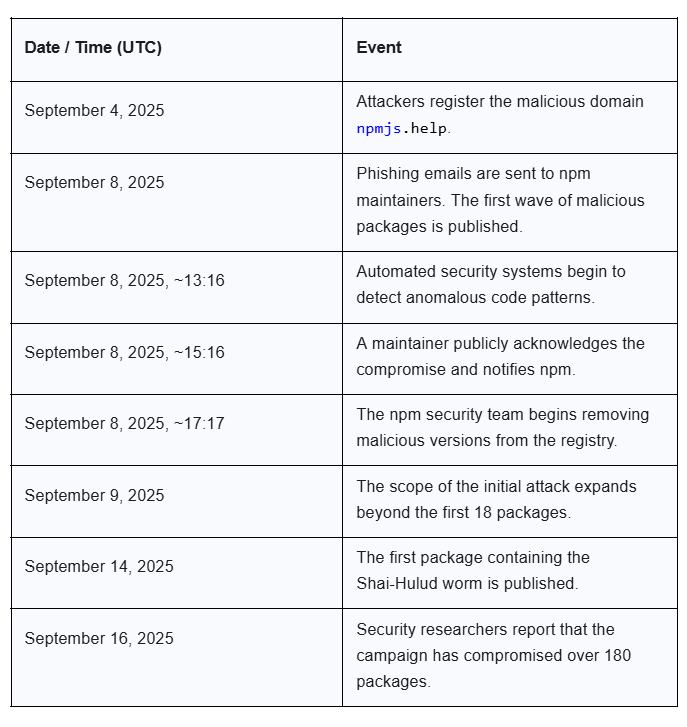
The malicious packages from the initial phishing campaign were live on the npm registry for only a brief period, ranging from two to six hours. This short window of exposure, however, was sufficient to allow thousands of automated build systems and developers to download the compromised code, underscoring the necessity for rapid detection and response in a continuous integration/continuous deployment (CI/CD) world.
The Shai-Hulud campaign represents a significant escalation in supply chain threats, distinguishing itself from previous attacks through its ability to self-propagate autonomously once the initial point of entry is breached.
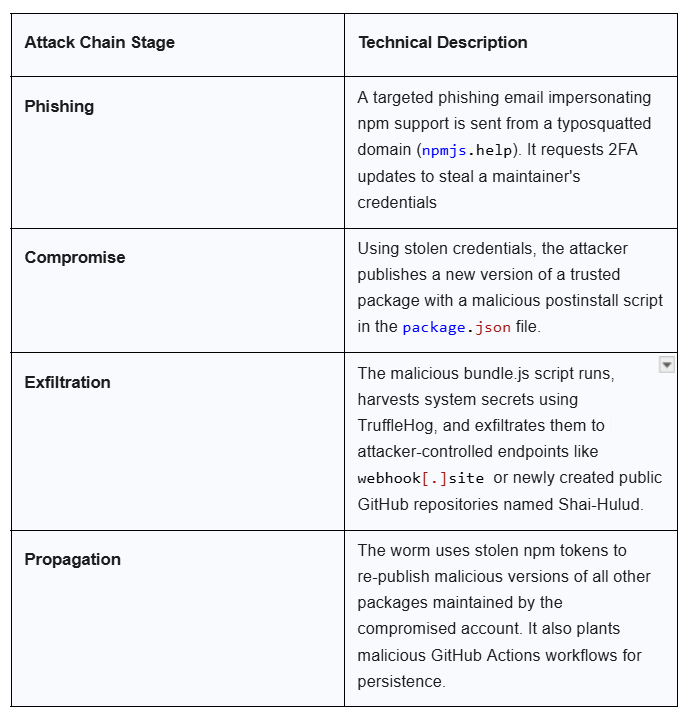
The core of the Shai-Hulud attack is a large and heavily minified JavaScript file named bundle.js, which is embedded into compromised packages. This script is designed to execute automatically during the package installation process via a malicious postinstall lifecycle hook in the package.json file. This design means that the malware activates and runs on a developer's machine or a CI/CD runner as soon as the infected package is installed, without requiring any action from the user.
The worm's operation is a multi-stage and automated attack chain that targets a wide range of sensitive data and propagates itself across the ecosystem.
Once executed, the payload begins to harvest sensitive data from the infected system. A key element of its sophistication is the use of TruffleHog, a legitimate, open-source secret-scanning tool, to search for credentials and tokens. The malware specifically targets npm authentication tokens, GitHub personal access tokens, and cloud service credentials (AWS, GCP, Azure). The use of a well-known, legitimate tool for a malicious purpose is a subtle but effective tactic to evade detection from security tools that might flag unknown executables.
Stolen data is exfiltrated to attacker-controlled destinations. The primary exfiltration methods include posting data to a hardcoded endpoint at webhook[.]site and committing a JSON dump of secrets to a newly created public GitHub repository named Shai-Hulud. To maintain a persistent foothold, the worm creates a malicious GitHub Actions workflow file (shai-hulud-workflow.yml) within compromised repositories. This workflow can be triggered to exfiltrate additional data and provide the attackers with ongoing access.
The most notable feature of the Shai-Hulud worm is its ability to self-replicate. Using the stolen npm tokens, the malware automatically enumerates all other packages maintained by the compromised account. It then downloads each package, injects its own malicious
bundle.js payload, and re-publishes a trojanized version back to the npm registry. This automated cycle transforms a single compromised account into a new, exponentially multiplying distribution vector, a capability that sets a new precedent for supply chain threats.

The widespread nature of the Shai-Hulud worm's self-propagation capability has had a significant impact on the open-source ecosystem, exposing several critical and systemic vulnerabilities.
The initial phishing-based attack against 18 packages quickly expanded into a far larger campaign. As of the latest reports, security researchers have identified over 200 compromised packages, demonstrating the worm's effectiveness at spreading laterally once a foothold is established. This includes packages with a high global footprint, such as
@ctrl/tinycolor with over 2 million weekly downloads, as well as several libraries from a high-profile organization like CrowdStrike. The incident confirms that even a relatively small compromise can ripple across thousands of projects and organizations.
The npm ecosystem's cultural and technical characteristics make it particularly susceptible to supply chain attacks. The community's tradition of relying on small and single-purpose packages creates a massive and often unmanageable dependency tree. A single project can transitively depend on hundreds of packages, making manual vetting an impossibility. Compounding this issue is the default behavior of npm install, which does not perform comprehensive integrity checks. While package-lock.json provides some integrity verification, it historically relied on the now-deprecated SHA-1 algorithm, which has known vulnerabilities. Furthermore, automated CI/CD pipelines can unknowingly pull the latest compromised version of a package, directly integrating the malicious code into a build without any human intervention.
This attack reveals a fundamental flaw in the prevailing open-source trust model. The pervasive assumption that a widely used package is inherently secure due to its community adoption is a liability. The attackers successfully poisoned this trusted source, forcing countless organizations to waste significant time and resources on an emergency response. This denial-of-service on industry productivity is a powerful attack in itself, as it undermines the foundation of trust that enables modern software development.
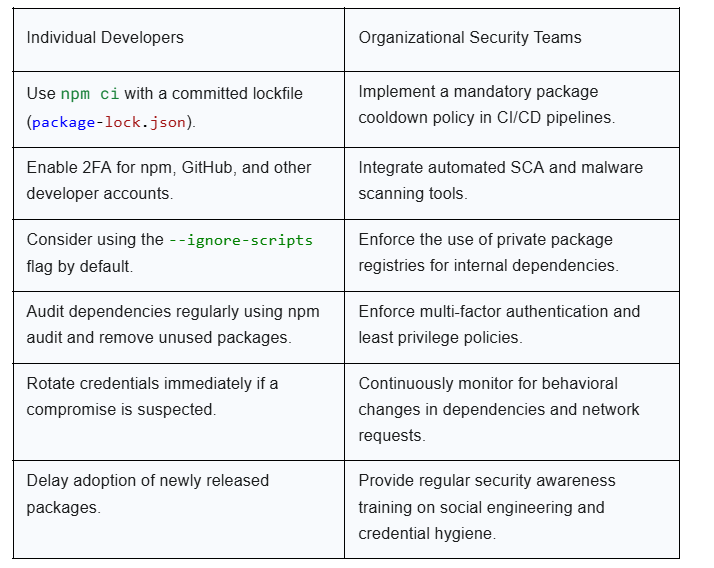
To counter the evolving threat from autonomous yet self-replicating malware, a new defensive posture is required. A shift from reactive security to a proactive and integrated approach is critical for both individual developers and organizations.
Individual developers are the first line of defense. The following practices are essential for securing development environments:
Organizations must move beyond individual best practices to implement a layered, systemic approach to supply chain security.
The Shai-Hulud attack is a wake-up call that the open-source threat landscape has evolved. The attacks are no longer simple one-off incidents; they are becoming more sophisticated, automated, and systemic. This new reality requires a collaborative and industry-wide response to build a more resilient digital foundation.
Ongoing efforts from organizations like the Open Source Security Foundation (OpenSSF) are crucial. Initiatives such as the Package Analysis project, which analyzes package behaviors for malicious activity, and the npm Best Practices Guide provide frameworks for hardening the ecosystem. These efforts must be coupled with a fundamental change in development culture.
The future of software security depends on treating open-source dependencies not as a given, but as a shared operational reality that requires continuous vigilance and proactive defense. By implementing in-workflow security controls and fostering a security-conscious culture, the industry can begin to address the systemic vulnerabilities that these attacks so effectively exploited.
If you’re concerned about how these kinds of attacks could impact your organization, we45 can help. Our team specializes in security training, threat modeling, and building resilient DevSecOps practices that reduce your risk from supply chain threats. By empowering developers and security teams alike, we45 ensures you’re not just reacting to incidents but proactively strengthening your software supply chain.
The September 2025 npm supply chain attack refers to a major incident where attackers compromised open-source JavaScript packages, using phishing and self-replicating malware to breach widely downloaded npm modules such as debug and chalk, impacting billions of downloads and many organizations.
Attackers started with phishing emails impersonating npm support, using a deceptive domain (npmjs.help) to trick maintainers into giving away credentials. Once inside, they published malicious versions of popular packages with crypto-stealing malware, and later, a worm called “Shai-Hulud” that spread automatically to hundreds more packages.
The Shai-Hulud worm is a self-propagating piece of malware that compromised more than 180 npm packages. After infecting one maintainer, it could harvest secrets such as npm and GitHub tokens, republish infected packages, and plant malicious GitHub actions using the same credentials, rapidly spreading throughout the ecosystem.
Notable packages like debug, chalk, ansi-styles, and many others with millions to billions of weekly downloads were affected. The list of compromised packages grew as more investigation continued, with new malware found in additional libraries nearly every day during the attack.
The malware targeted cryptocurrency wallets and browser extension APIs, hijacking addresses and transactions. In the case of Shai-Hulud, it exfiltrated credentials and secrets through automated workflows and GitHub repositories, while also obfuscating its activity to evade detection.
The npm ecosystem relies on open-source maintainers who often control many interconnected packages. Attackers exploited this by breaching one maintainer, then leveraging that access to infect all packages they managed. With automatic propagation, the attack quickly cascaded across thousands of projects.
Reports indicate that financial losses were relatively small, limited to a few hundred dollars in stolen cryptocurrency. However, the real cost was widespread disruption, lost developer hours, emergency audits, and crisis response efforts across thousands of organizations.
Best practices include immediately rotating all npm and GitHub credentials, auditing dependency lists, reverting or updating affected packages, using lockfile-only installs, and monitoring for indicators of compromise (IoCs) and suspicious package updates.
Josh Junon, maintainer of core libraries like debug and chalk, was among the first to be compromised, after falling for a phishing email while distracted and using a mobile device. His account takeover was a key turning point for the attack.
The attack is still ongoing as new compromised packages and tactics are discovered daily. Security advisories, package deprecations, and new indicators of compromise are being published regularly—developers should remain vigilant and keep their workflows up to date with the latest security guidance.