
In recent years, organizations have experienced significant breaches stemming from exposed AWS credentials in public repositories. GitGuardian's research reveals the scope of the problem: 23.8 million credentials were detected in public GitHub repositories in 2024, marking a 25% increase from 2023.
More concerning: 70% of these secrets remain active and exploitable. For security engineers running distributed systems, the math is brutal: 50 microservices generate 200+ credentials when you account for databases, message queues, APIs, and inter-service auth. Manual rotation at that scale is like trying to change tires on a moving car.

Most teams treat secrets like configuration files. They're not. They're dynamic infrastructure that needs lifecycle management, automated rotation, and zero-trust access patterns. When your platform spans Kubernetes clusters, serverless functions, and CI/CD pipelines across three cloud providers, hardcoded credentials become architectural debt.
The hidden cost? Average time to detect a leaked credential: 292 days. By then, attackers have pivoted three times and exfiltrated your customer database.
Don't migrate blind. Scan everything first:
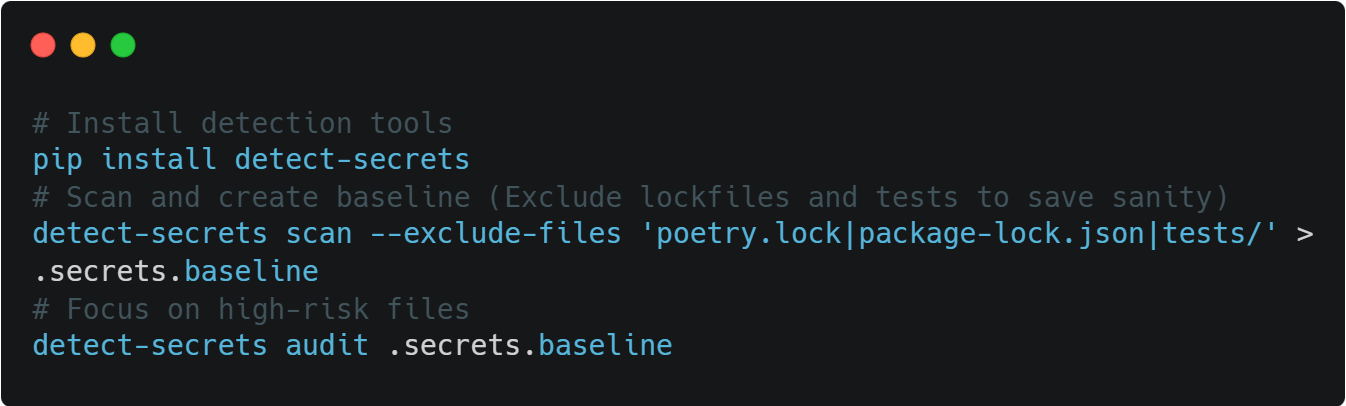
This finds what you have. Now prioritize ruthlessly:
Store your first secret:
.png)
Update your application to fetch at runtime:
.png)
The difference? Environment variables are visible in your AWS console to anyone with read access. SDK retrieval requires explicit IAM permissions and leaves an audit trail.
Manual credential rotation fails at scale because humans forget, systems break during updates, and coordinating changes across 50 services causes outages. Automation eliminates all three problems.
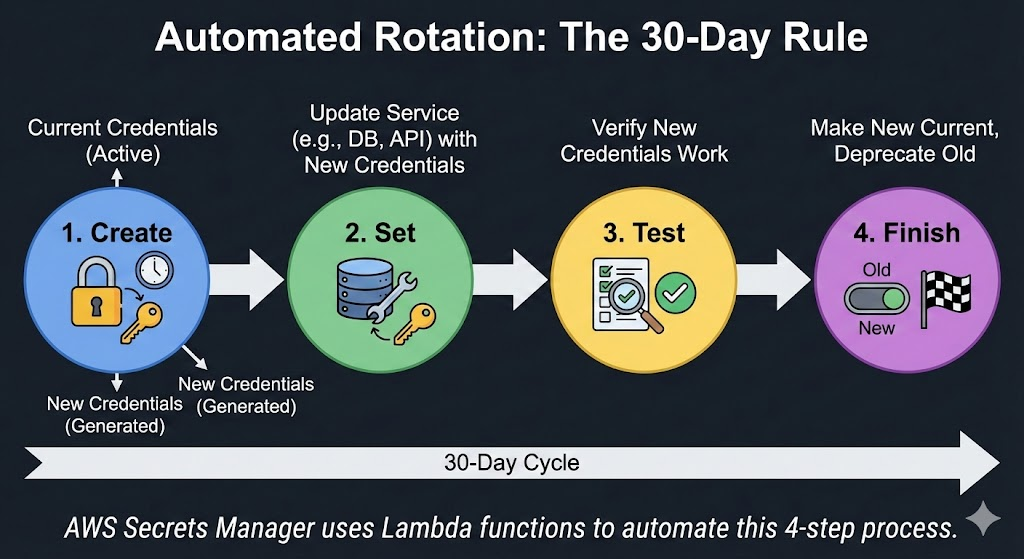
AWS Secrets Manager rotates secrets using Lambda functions that implement a four-step process:
This allows for zero-downtime rotation, but only if your application handles it correctly. The Trap: Most database drivers use connection pooling. If your app holds a connection open for 6 hours, and the password rotates every hour, your app will eventually crash when it tries to use that stale connection.
You must configure your connection pool max_lifetime to be shorter than your rotation window (e.g., if rotation is 30 days, set connection lifetime to 12-24 hour) to ensure apps naturally cycle their credentials.
.png)
Set rotation to 30 days for databases (balances security vs. operational risk), 7 days for service account tokens (low-impact, high-security), and 90 days for external API keys where you depend on vendor support.
GitHub Actions with OIDC eliminates long-lived access keys entirely. Instead of storing AWS credentials that live forever, your workflow gets temporary credentials that expire in an hour. Create an IAM role with this trust policy so GitHub can assume it
The setup:
.png)
No secrets stored in GitHub. Credentials expire automatically. Audit logs show exactly which workflow accessed AWS.
Instead of storing secrets in Git (bad) or manually creating Kubernetes secrets (doesn't scale), sync from centralized stores automatically.
Define what you want:
.png)
External Secrets Operator creates native Kubernetes secrets that your pods consume normally. When you rotate credentials in AWS Secrets Manager, ESO syncs the change within 15 minutes. Your pods automatically get updated secrets without manual intervention.
Lambda environment variables are encrypted at rest but visible in plain text in the console. For PCI DSS or HIPAA compliance, this fails audit.
Better approach - fetch at runtime with caching:
.png)
This adds 20ms latency on cache miss (once per 5 minutes) but keeps secrets out of your Lambda configuration entirely.
Pre-commit hooks block secrets before they hit Git:
.png)
Developers can't commit without scanning. False positives get marked in the baseline file.
For real-time protection, GitGuardian scans public and private repositories continuously, detecting 400+ secret types. When leaks are found, trigger immediate rotation:
.png)
AWS Secrets Manager costs $0.40/secret/month. For 500 secrets: $2,400/year.
API calls cost $0.05 per 10,000 requests. If you don't implement client-side caching (as shown in the Python example above) and your app fetches the secret on every HTTP request, a high-traffic service can easily rack up $1,000+ in API fees. Cache locally, refresh on failure.
But the real value isn't the avoided breach cost—it's sleeping at night knowing your credentials rotate automatically, leaks get caught in seconds, and your audit trail is complete.
What Actually Works
The difference between getting breached and staying secure comes down to three practices:
Everything else: compliance frameworks, vendor selection, architecture patterns supports these fundamentals. Start with your most critical secrets (production databases, payment processors), automate their rotation first, then scale the pattern.
The goal isn't perfect security. It's making exploitation harder for attackers than hitting your competitors. In a world where 10 million secrets leak annually, being slightly better than average might be the best ROI decision you make this year.
Transitioning to a zero-static-credential architecture demands an objective review of your current cloud-native posture, CI/CD pipelines, and secret deployment patterns. To move from conceptual understanding to a hardened, auditable reality, security leaders should begin with a precise external assessment. we45's Cloud Security Assessment services are designed to provide this actionable clarity, ensuring your strategy is implemented with maximum security impact and minimal operational friction.
Secrets are sensitive credentials and tokens needed to access resources—database passwords, API keys, AWS access keys, payment processor tokens, encryption keys, and OAuth tokens. Unlike regular configuration (which is non-sensitive), secrets must be protected, rotated regularly, and access-controlled strictly.
Environment variables are visible in plain text to anyone with console access to your cloud account. They're not rotated automatically, difficult to audit, and appear in logs during crashes or debugging. Centralized secret management (like AWS Secrets Manager) requires explicit IAM permissions, maintains audit trails, and enables automated rotation.
No. Even small teams with 5-10 microservices need centralized secret management. The operational overhead of manual rotation and tracking grows exponentially with scale. Starting early prevents costly migrations later.
AWS Secrets Manager costs $0.40/secret/month plus $0.05 per 10,000 API calls. For 500 secrets storing 1 month of data: approximately $2,400/year in storage. API costs depend on your application's fetch frequency—caching keeps costs down. Compare this to a single breach's remediation cost (average $4.29M for data breaches in 2024) and it's negligible. Frequently Asked Questions (FAQs) for Cloud Secrets Management
The primary risk is the exposure of active AWS credentials in public repositories, with 23.8 million credentials detected in 2024. More concerning is that 70% of these leaked secrets remain active and exploitable, giving attackers a critical access point. The average time to detect a leaked credential is a dangerous 292 days.
Manual rotation processes fail at scale because they introduce human error, cause system outages during updates, and cannot keep pace with the growth of distributed systems. A modern application with 50 microservices can generate over 200 credentials, making manual coordination impossible to manage without automation.
The recommended strategy is the 30-day rule for high-impact secrets like database passwords. Use a centralized secret manager, such as AWS Secrets Manager, with a serverless function to automate a four-step rotation process: Create, Set, Test, and Finish. Crucially, application connection pools must be configured with a maximum lifetime shorter than the rotation window to prevent crashes from stale connections.
OpenID Connect (OIDC) eliminates the need to store long-lived static AWS access keys in CI/CD pipelines. Instead, your workflow, such as GitHub Actions, requests temporary credentials that expire quickly (e.g., in an hour). This requires an attacker to compromise both your CI/CD system and your cloud console, significantly improving defense in depth.
Do not rely on Lambda environment variables, as they are visible in plain text in the console, posing a compliance risk. A better approach is to fetch secrets at runtime from a secrets manager, using an SDK with built-in caching. This keeps sensitive data out of the function’s configuration entirely, with minimal latency impact.
AWS Secrets Manager costs approximately $0.40 per secret per month. For 500 secrets, the annual storage cost is about $2,400. This is a negligible expense when compared to the average cost of a data breach, which was $4.29 million in 2024. The real value is the audit trail, automated security, and the avoidance of a catastrophic breach.